Hello, I wrote this tutorial to represent the parameters to implement to successfully implement smart card authentication in RDS.
In this environment, RDS publishing servers is in a different Direcory Active Forest from users.
In this context, here are all the steps you need to take to properly set up active Directory and your RDS farm to allow this second authentication factor.
Attention I do not explain how to install the solution RDS, i detail all the prerequisites for smartcard authentication in a multi domain environment, multi forest works.
Environment description
ADDS
First forest AD DS : AD.LOCAL
- One domain controller: DC01.ad.local
- PKI
- Domain name: AD.LOCAL
- Content:
- Users
- Security groups
Workstation
Second forest AD DS : FOREST.LOCAL
- One domain controller: DC10.forest.local
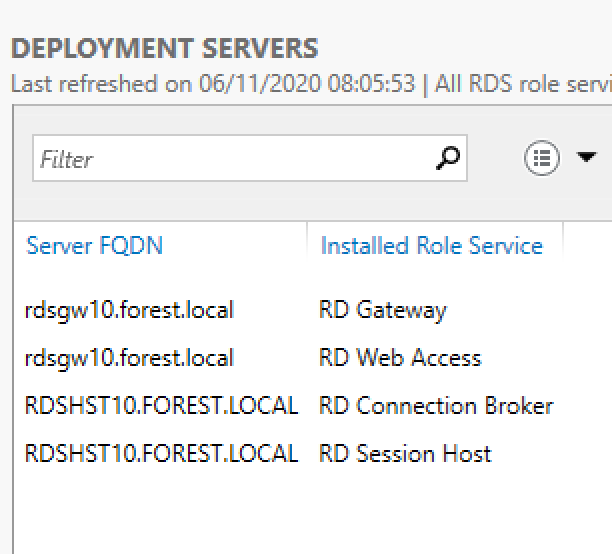
- Infra RDS details:
- Rdshst rôles Broker et Host
- Rdsgw rôles gateway et Web access
Trust relationship AD DS
Two-way trust
Infra RDS
Windows server services
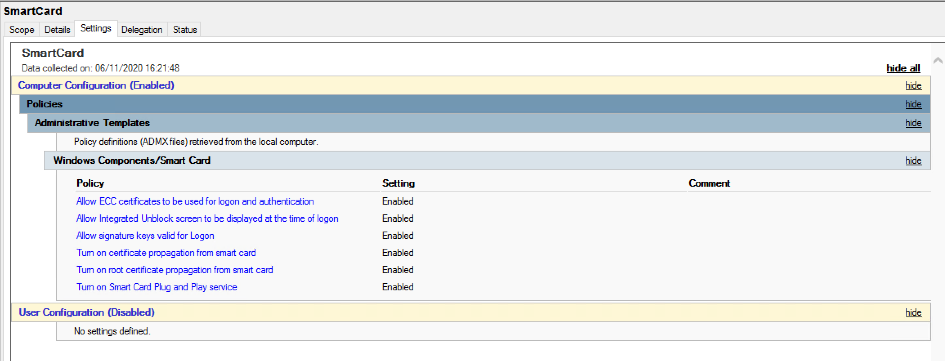
Set smartcard logon service to start automatically and start the service on all servers of the RDS infra.
Remote Desktop Services
RD Web Access details
Web access URL: rds10.forest.local
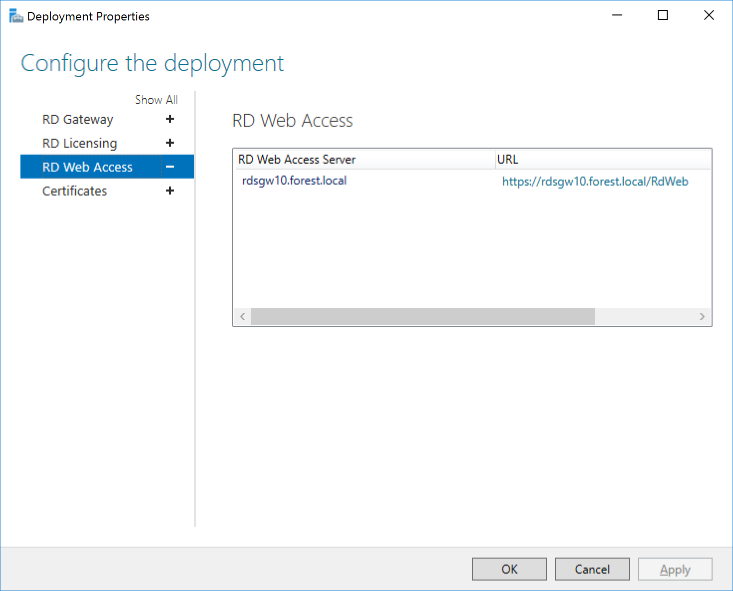
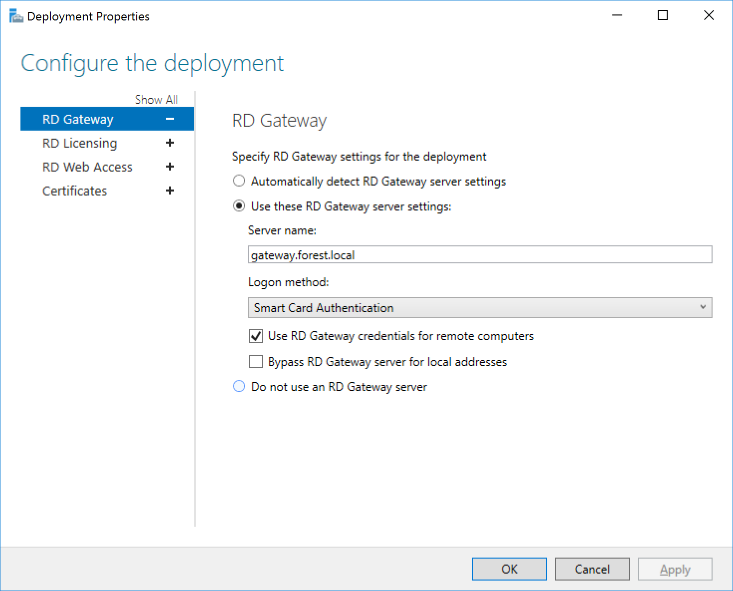
RD Gateway details
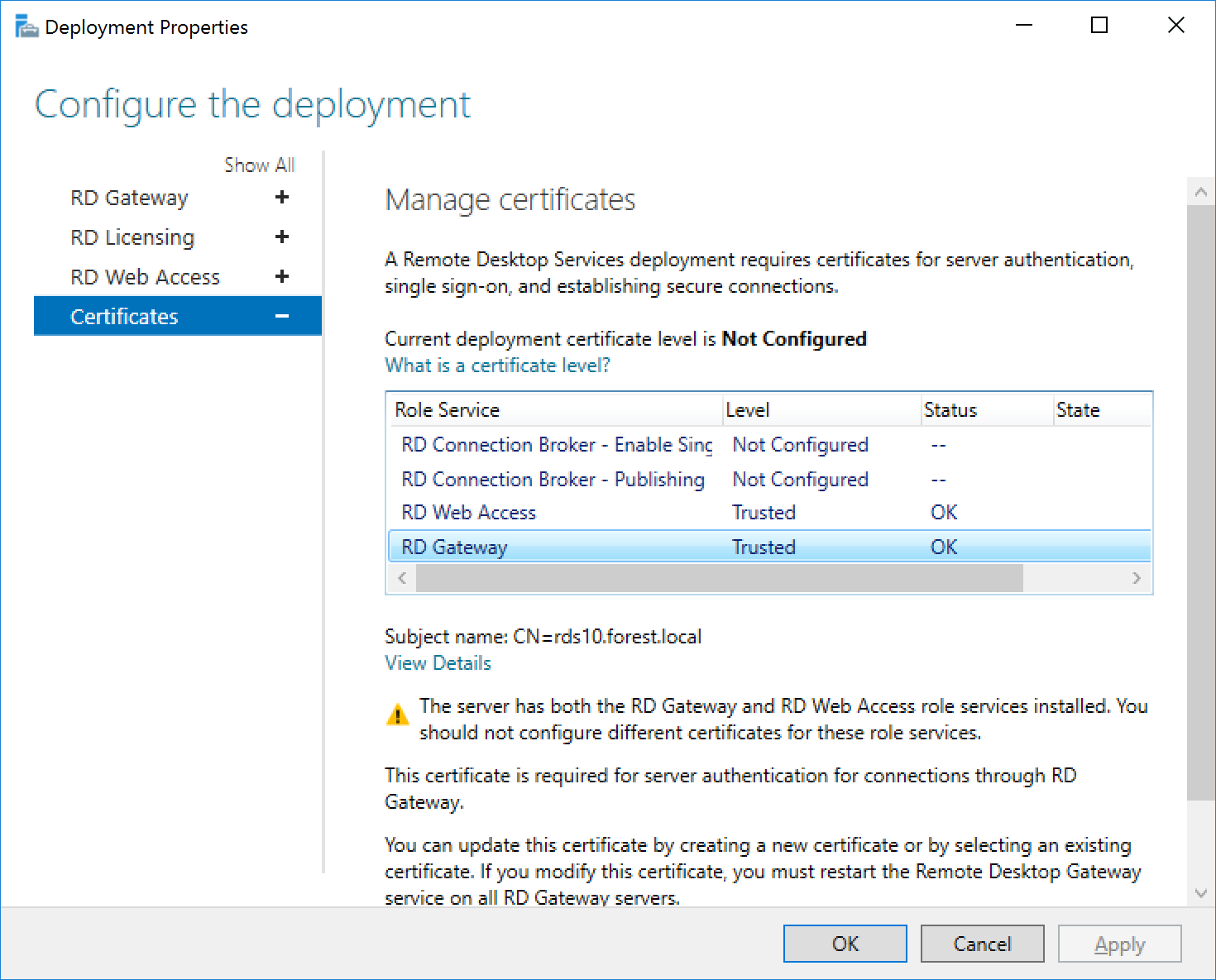
Certificates deployment details
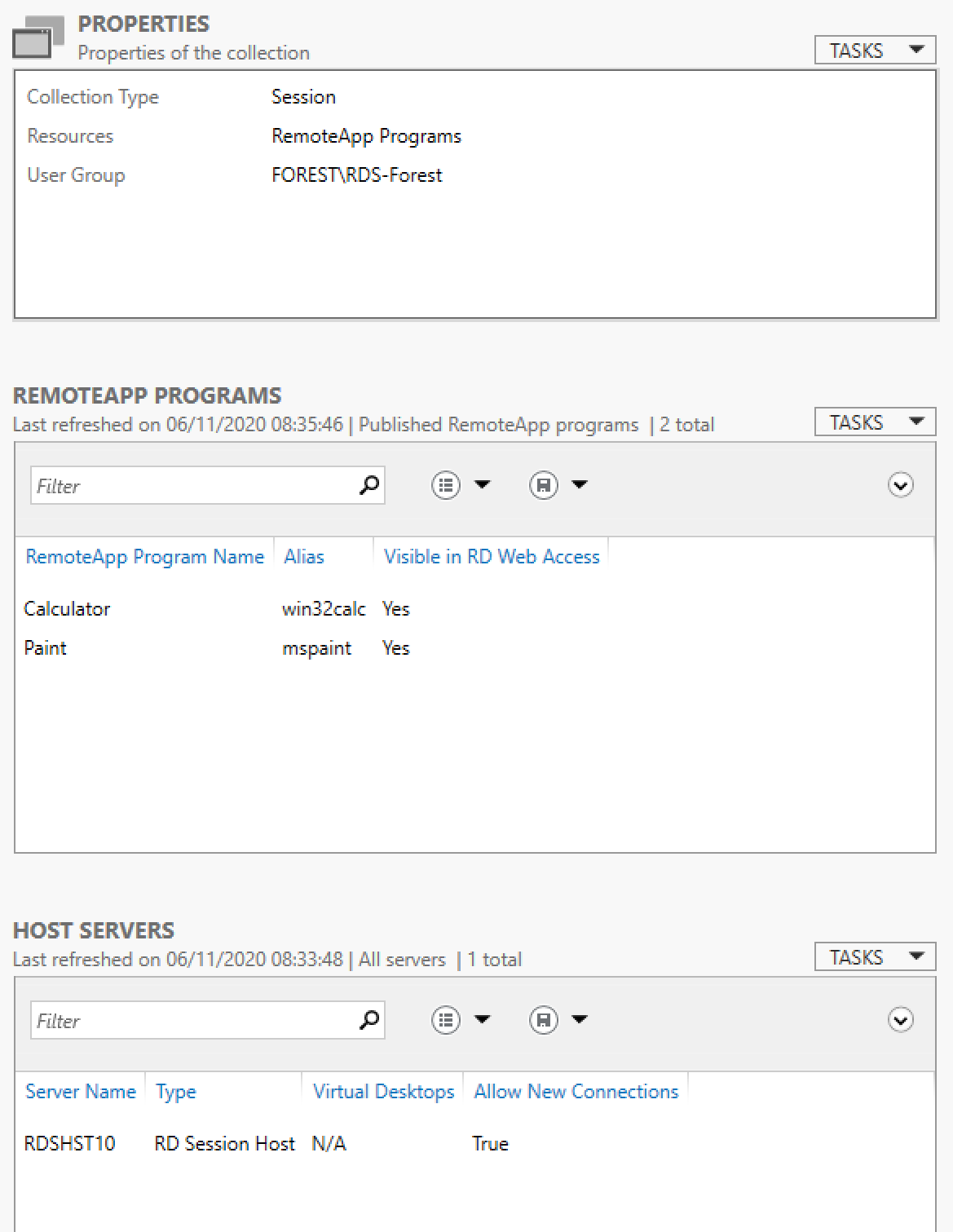
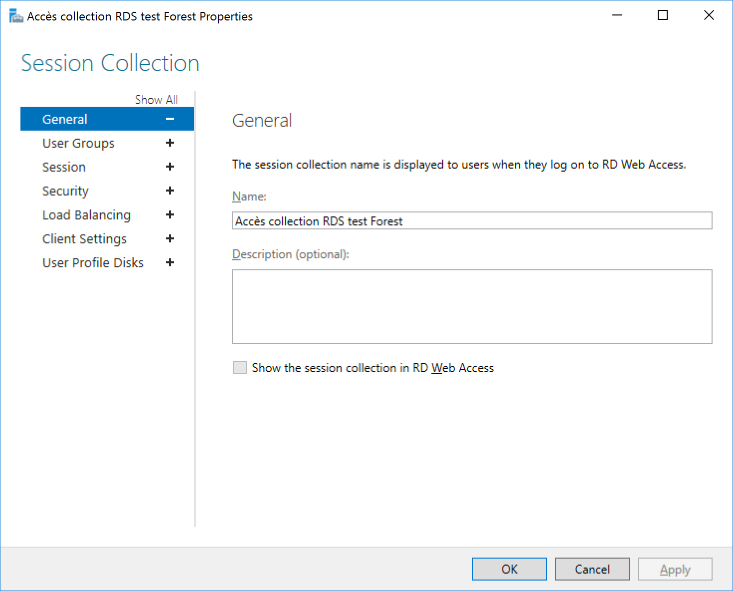
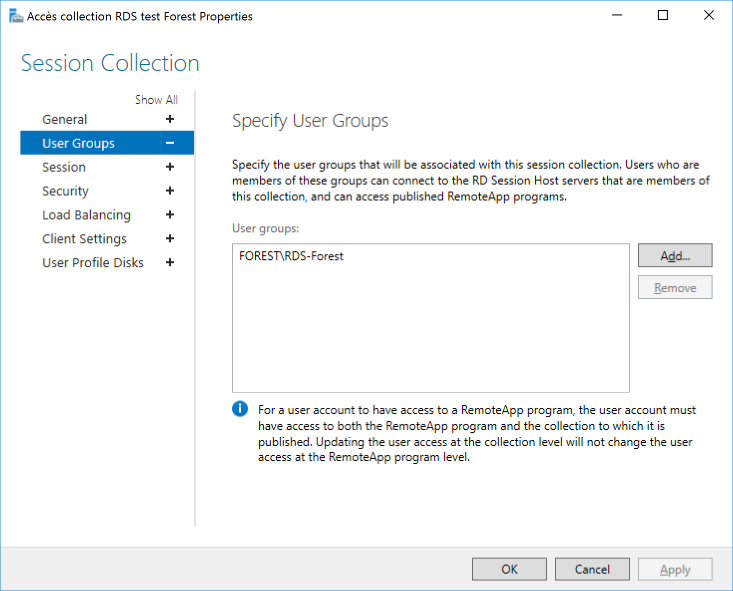
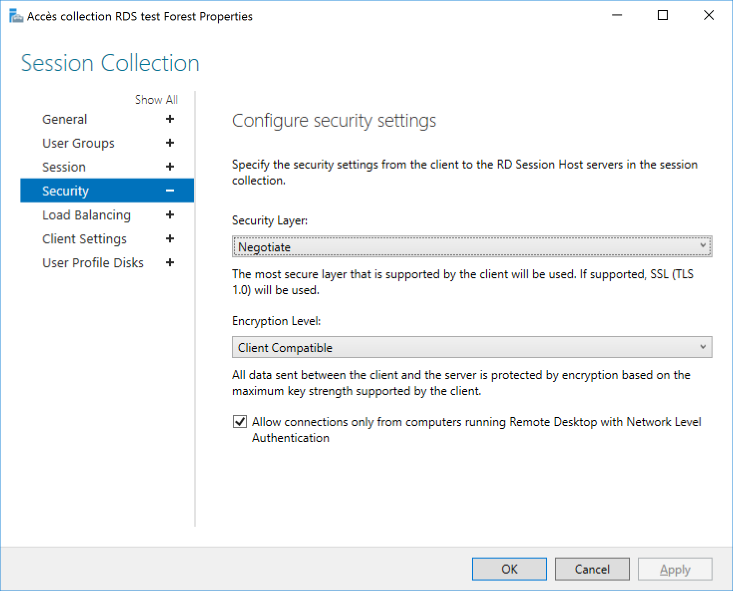
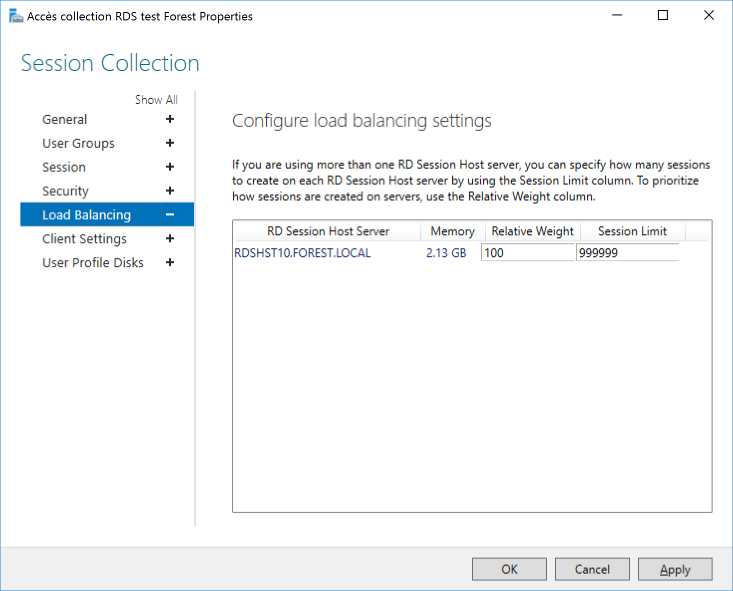
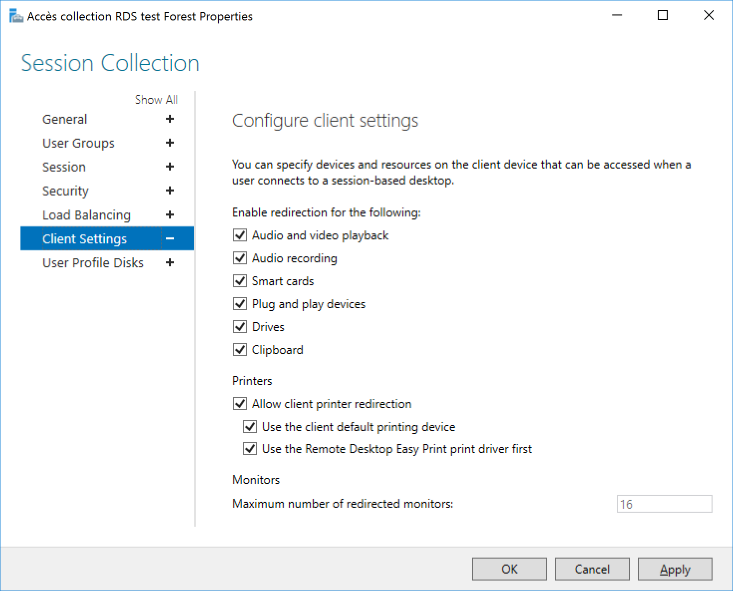
Properties of the collections
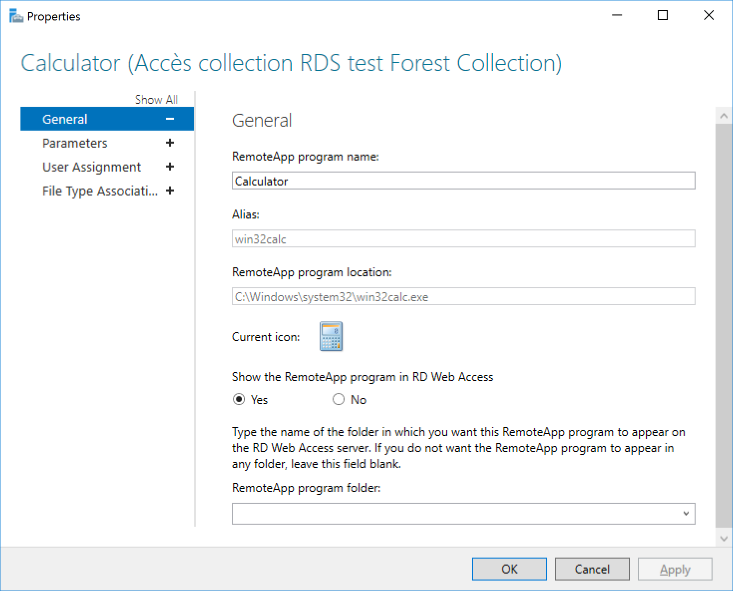
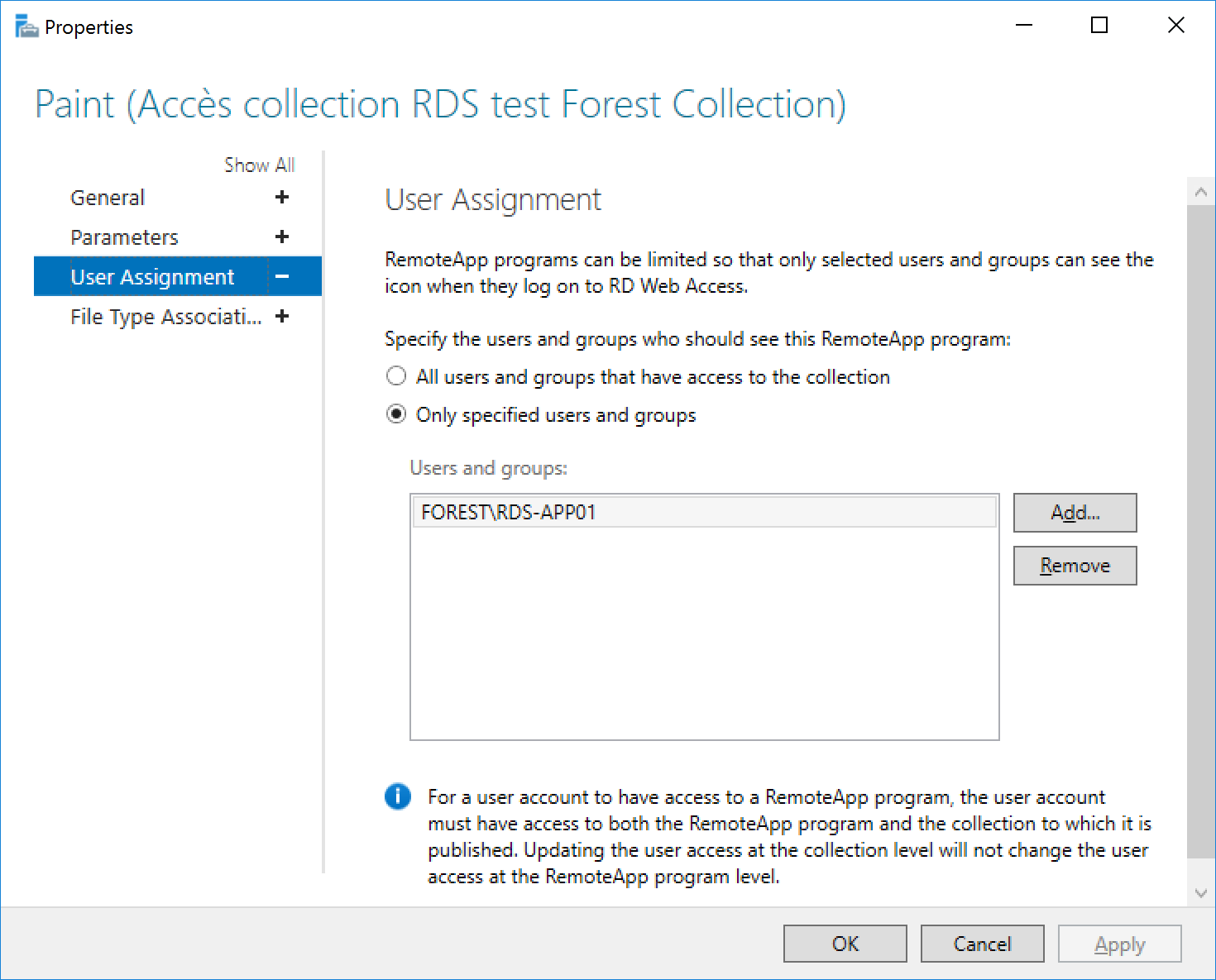
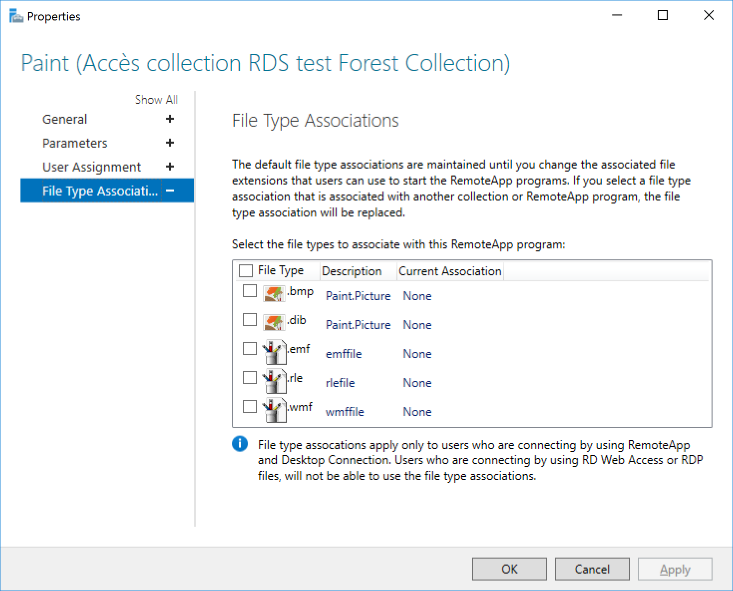
Remote APPS settings
Calculate
MsPaint
RD Gateway Manager settings
External URL : gateway.forest.local
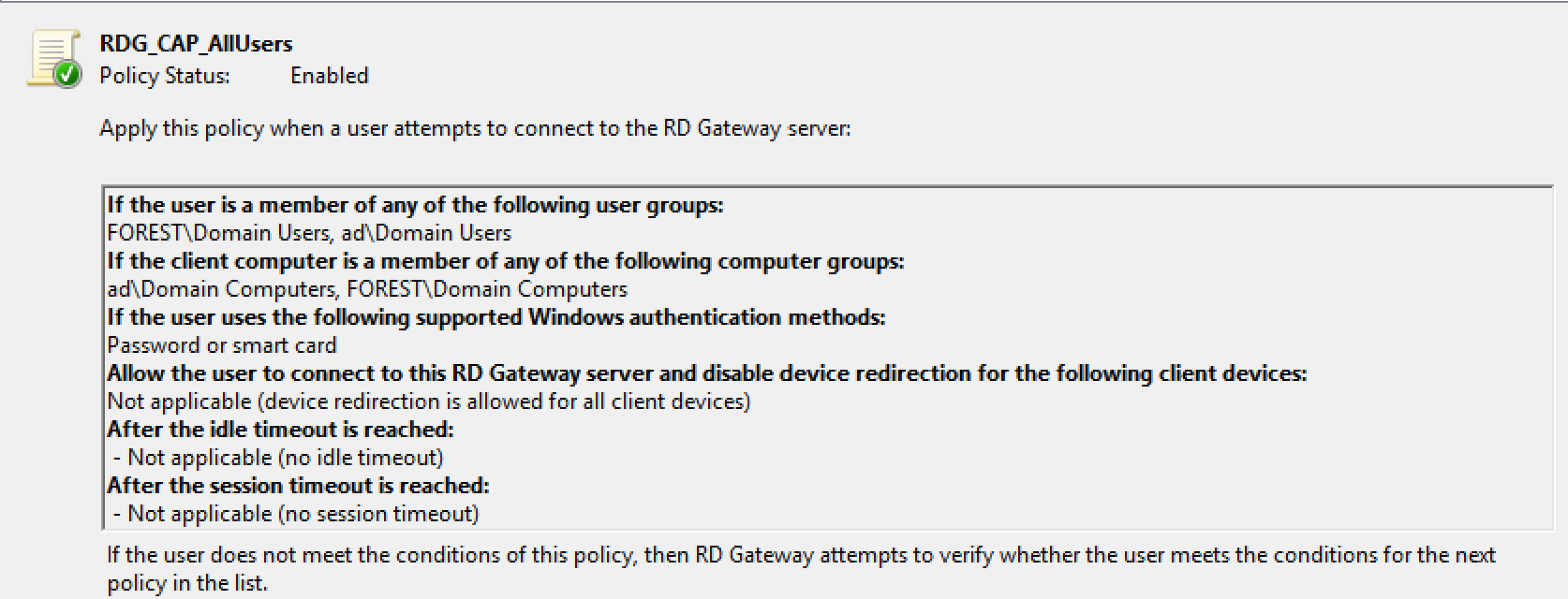
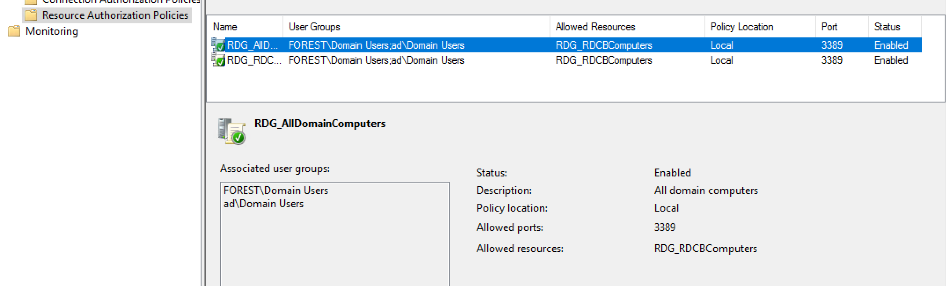
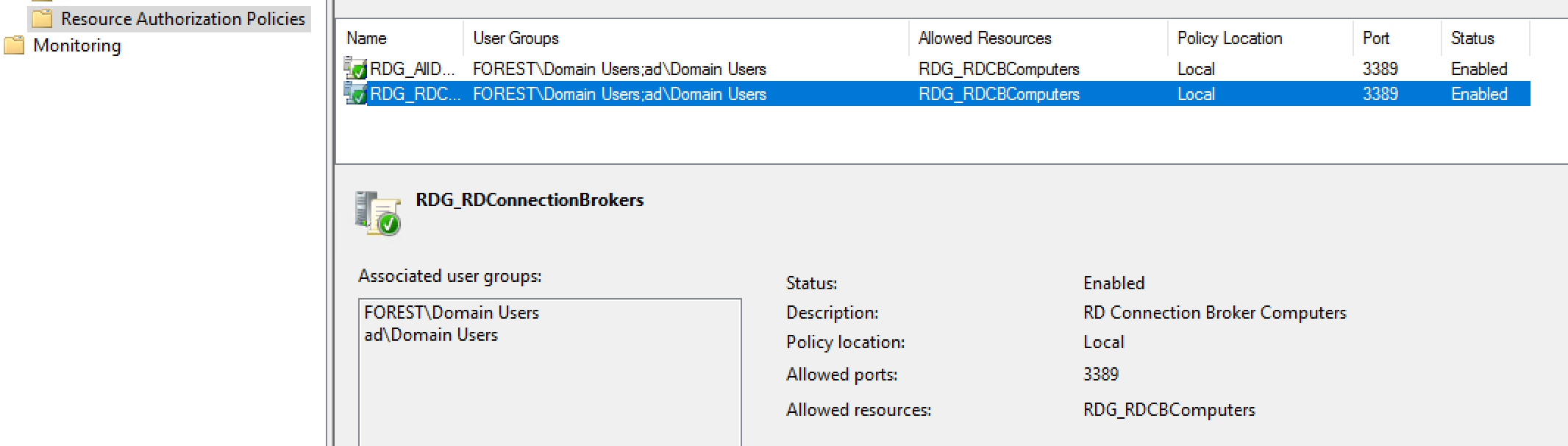
Policies settings
RDG_CAP_AllUsers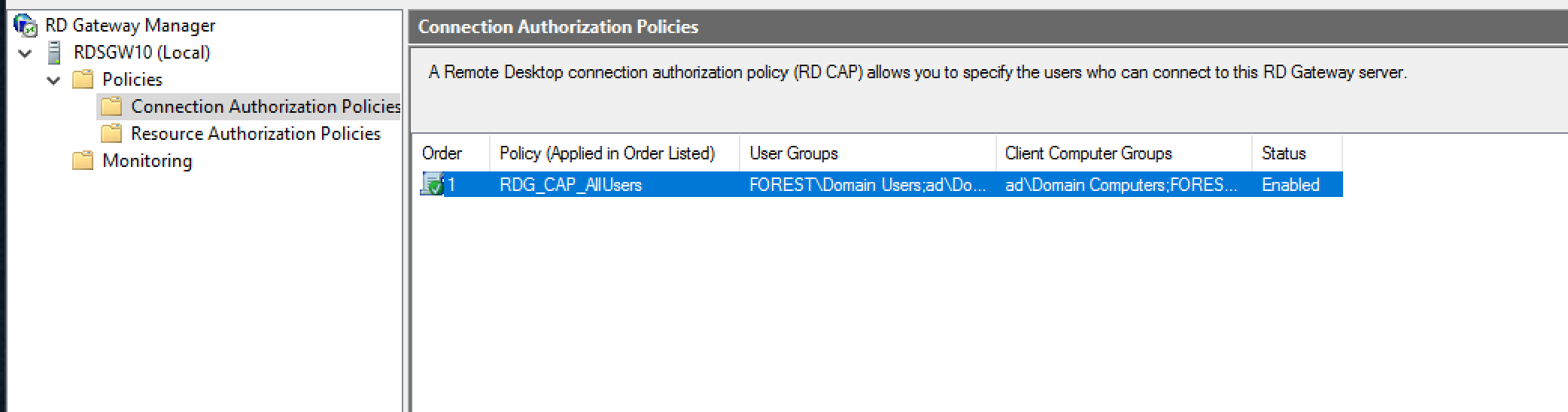
RDG_AllDomainComputers
RDG_RDConnectionBrokers
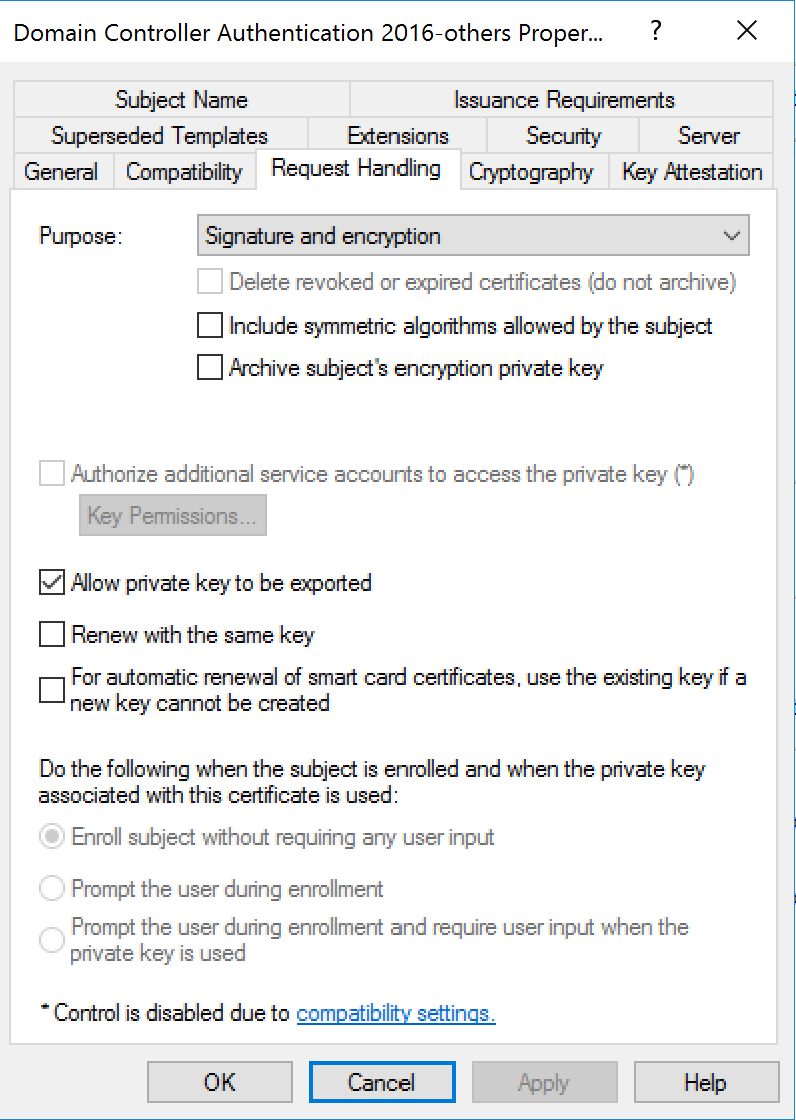
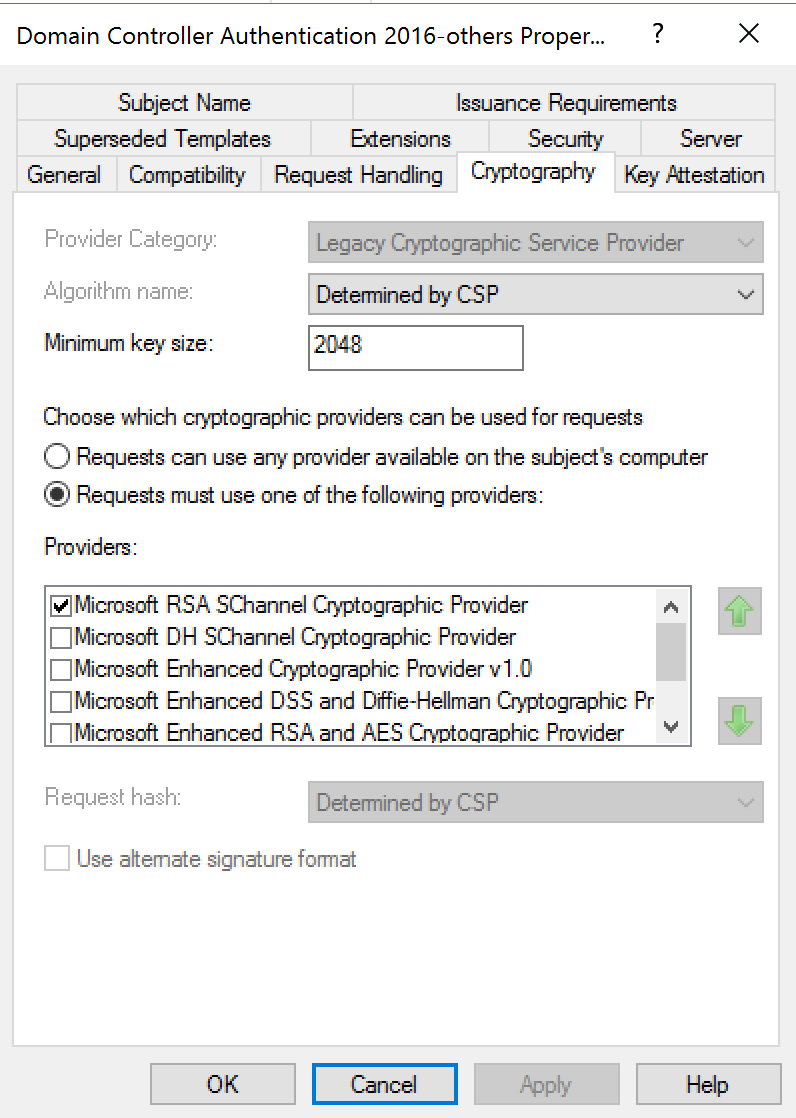
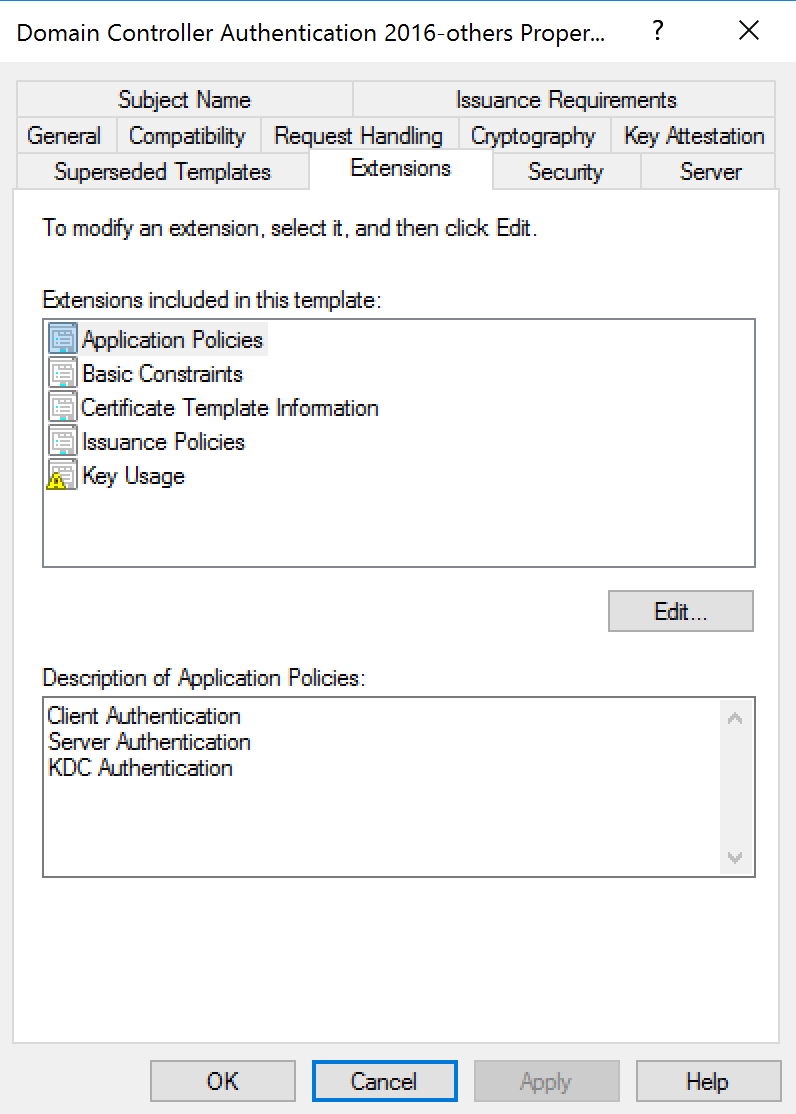
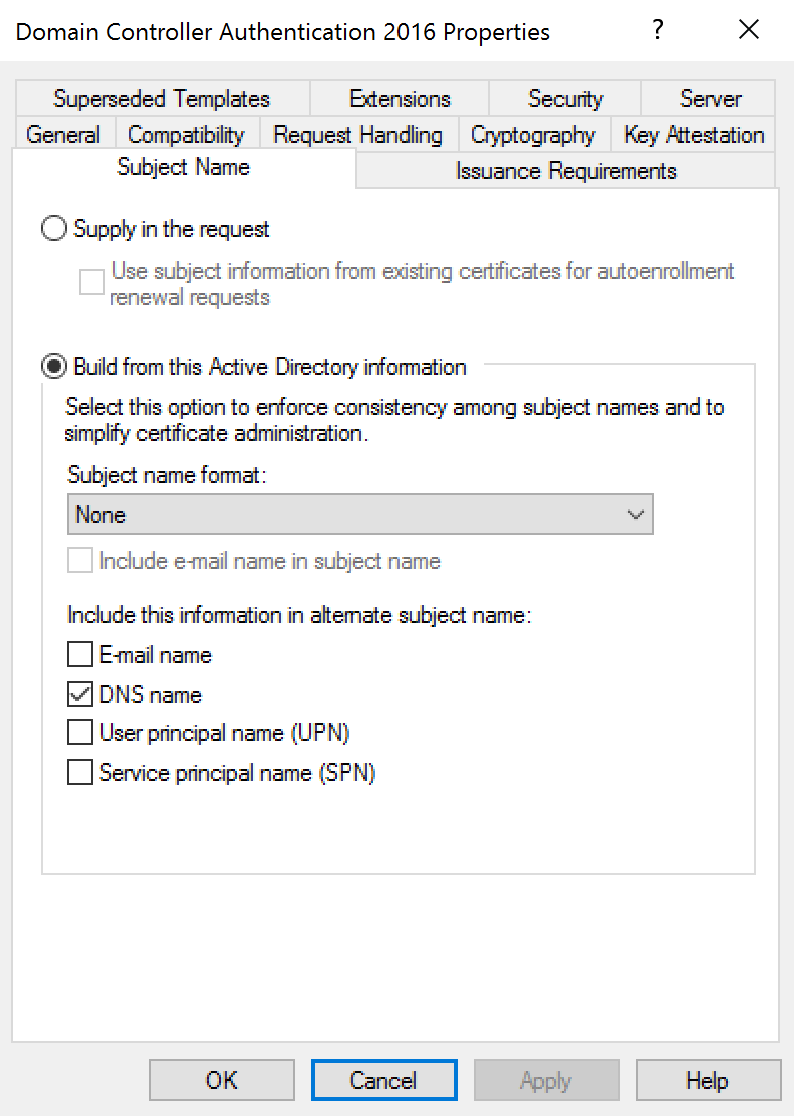
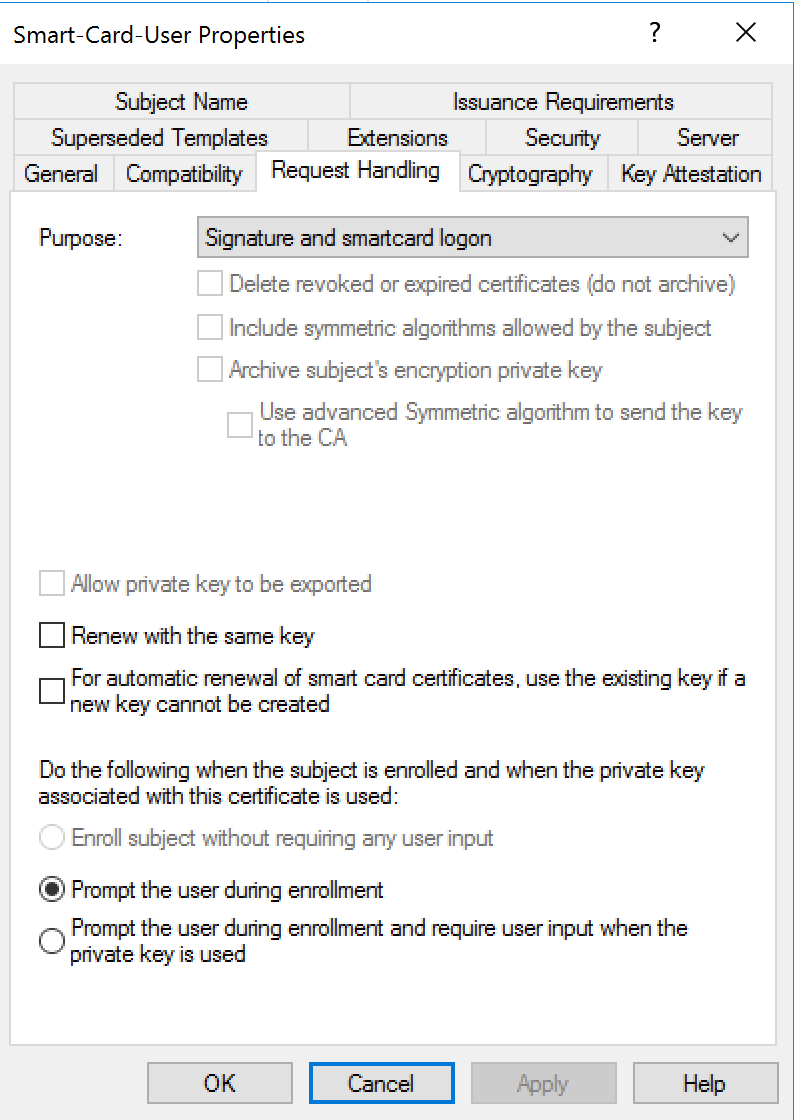
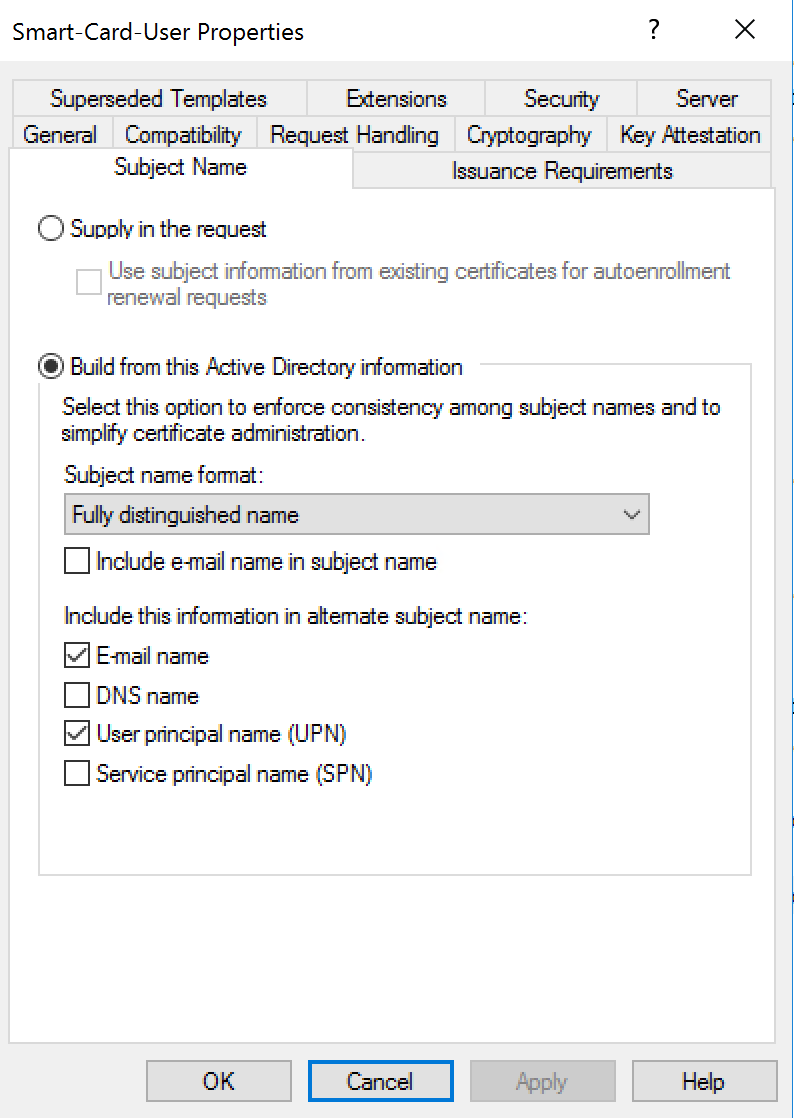
Certificates models
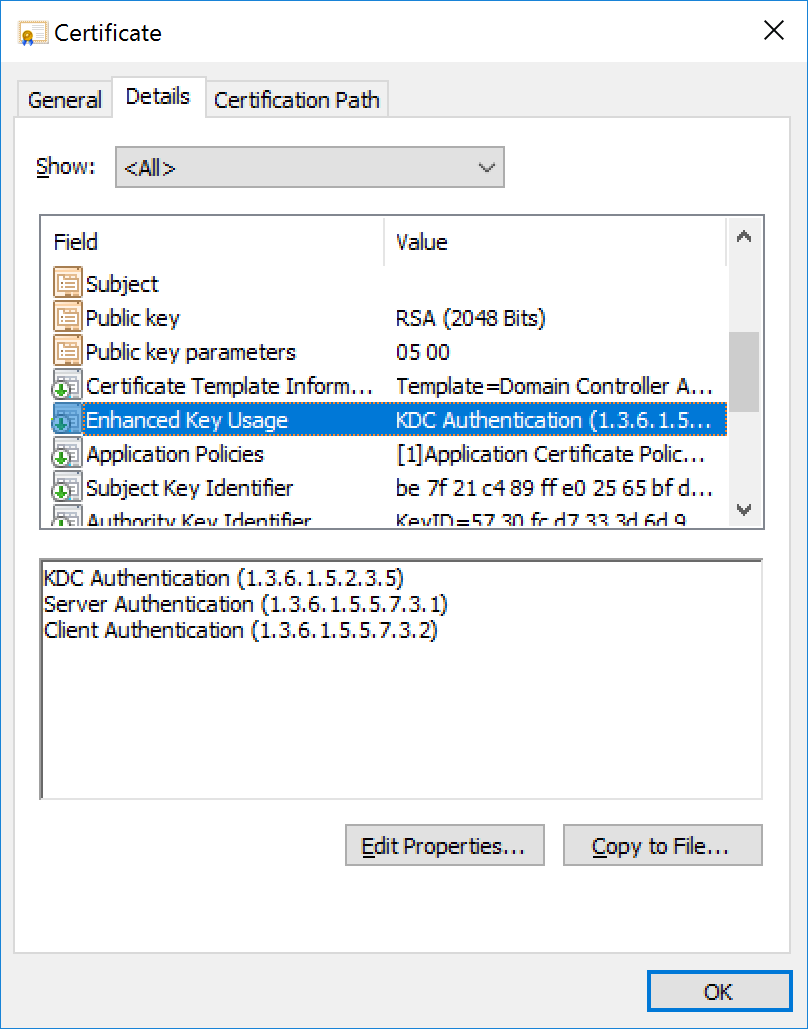
Model domain controller
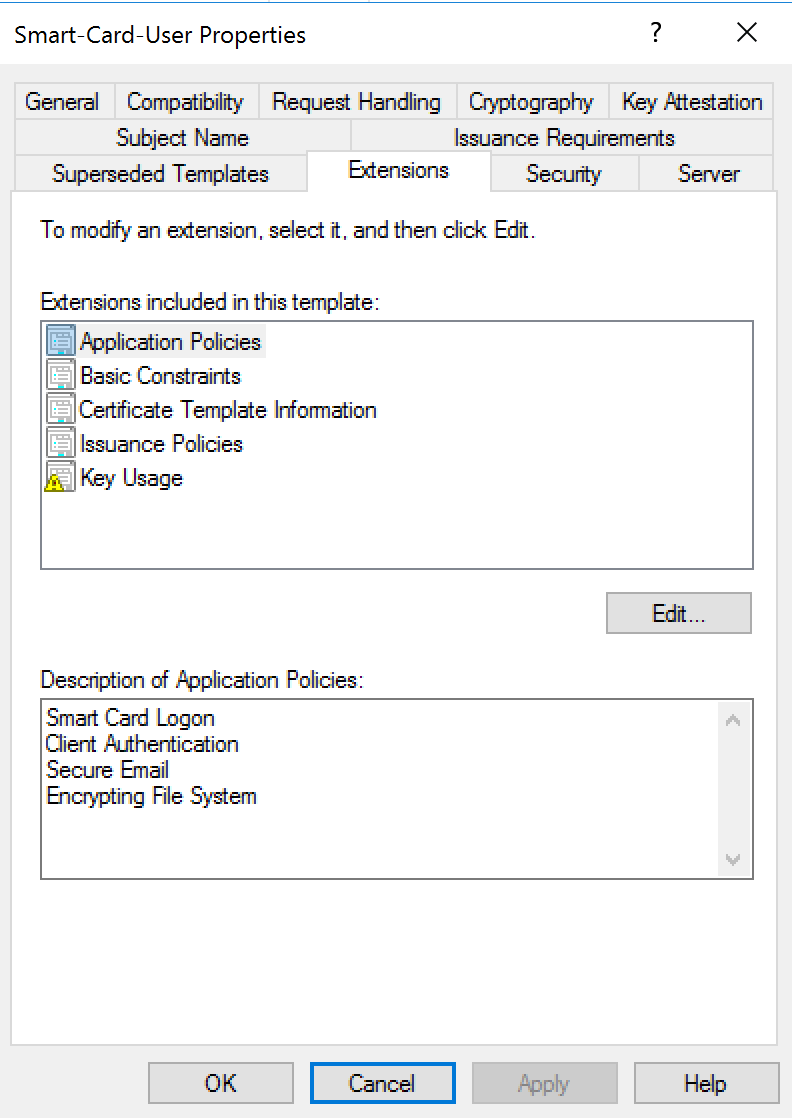
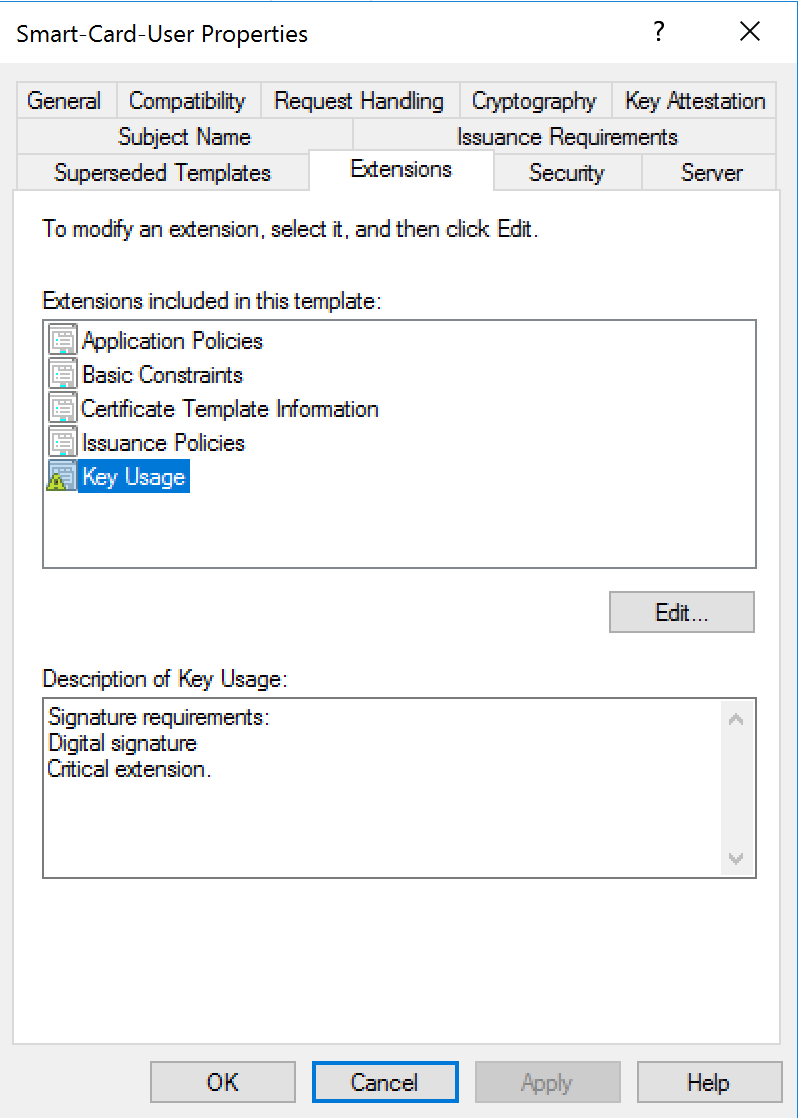
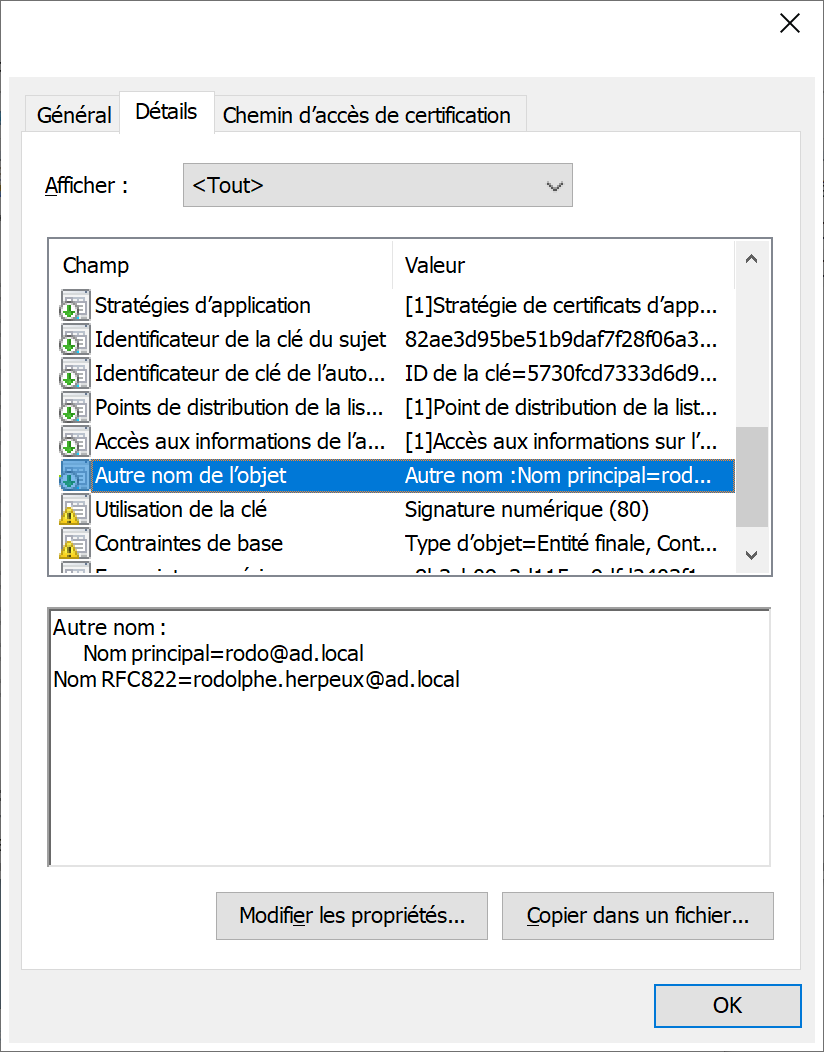
Model Smartcard
Requirements and references
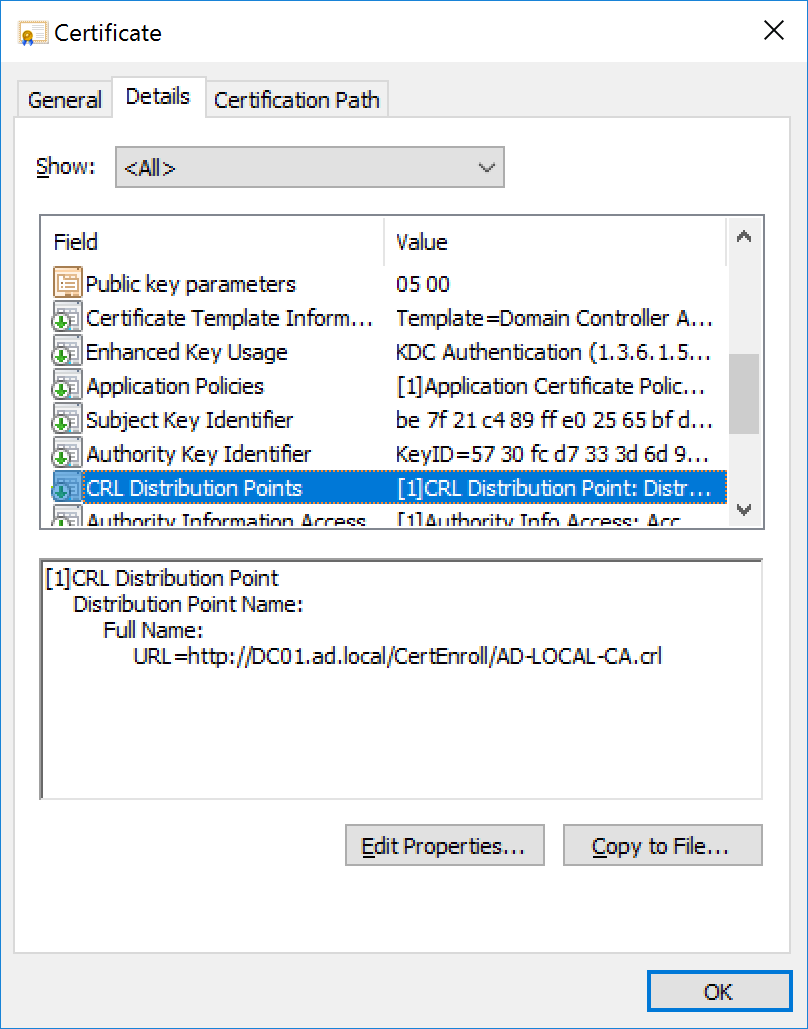
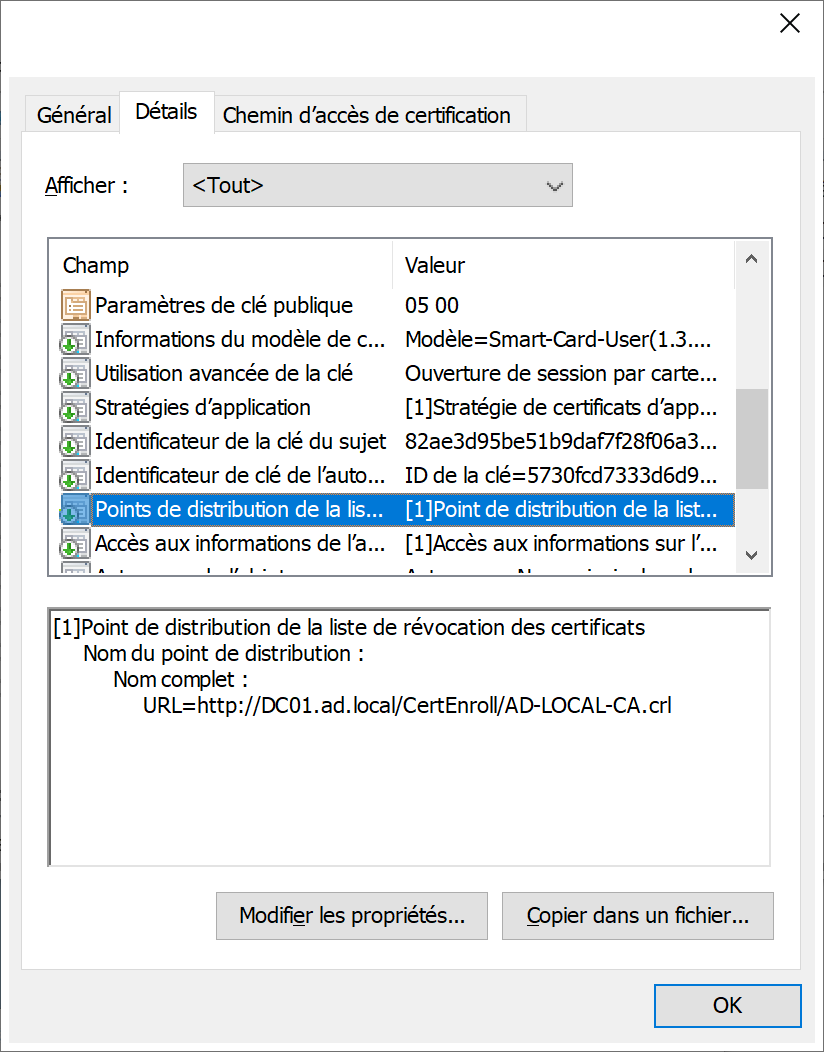
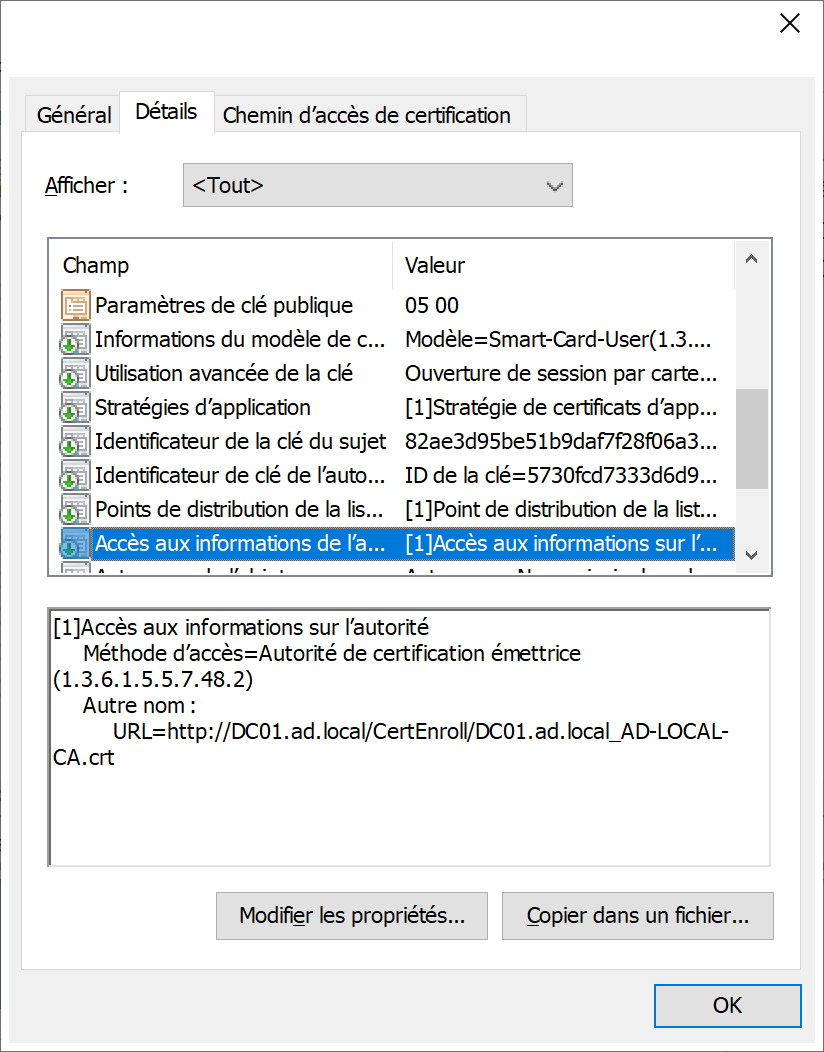
Add the third party issuing the CA to the NTAuth store in Active Directory.
The smart card logon certificate must be issued from a CA that is in the NTAuth store. By default, Microsoft Enterprise CAs are added to the NTAuth store.
If the CA that issued the smart card logon certificate or the domain controller certificates is not properly posted in the NTAuth store, the smart card logon process does not work. The corresponding answer is “Unable to verify the credentials”.
https://docs.microsoft.com/en-ca/troubleshoot/windows-server/windows-security/enabling-smart-card-logon-third-party-certification-authorities
https://docs.microsoft.com/en-us/windows/security/identity-protection/smart-cards/smart-card-and-remote-desktop-services
Command lines executed in forest.local
- certutil -dspublish -f c:tempCA.cer NTAuthCA
- certutil -enterprise -addstore NTAuth c:tempCA.cer
certutil -addstore -enterprise NTAUTH “C:Tempdc01.ad.local.cer”, need to be verify without this certificate
Group Policy Domain
Domain forest.local
Demonstration
Test with APP01 Account for Paint application
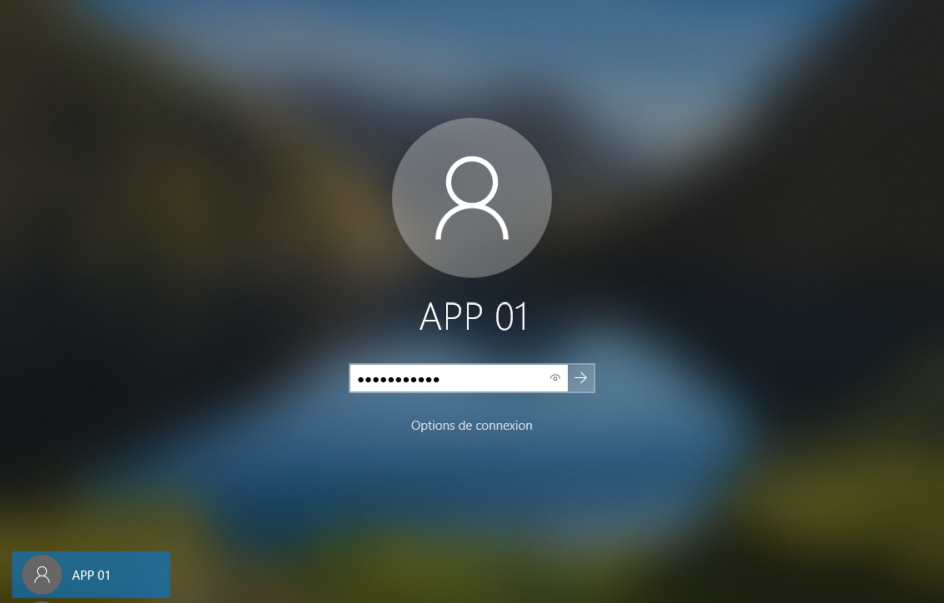
Open session on workstation Win10 with account user APP01
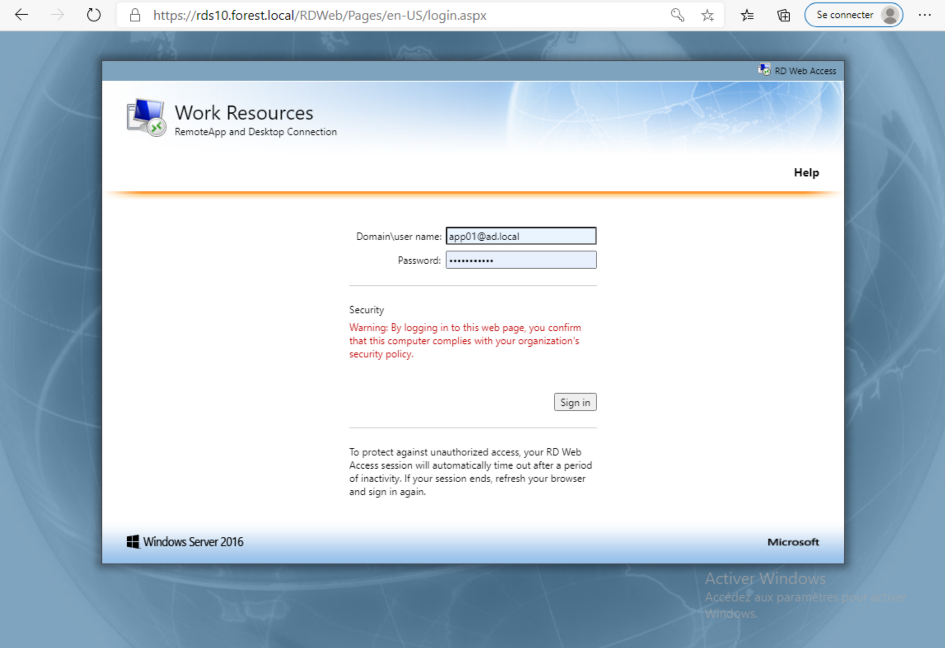
 Open Edge browser and browse on url https://rds10.forest.local/rdweb portal
Open Edge browser and browse on url https://rds10.forest.local/rdweb portal
 Open session with user account APP01
Open session with user account APP01
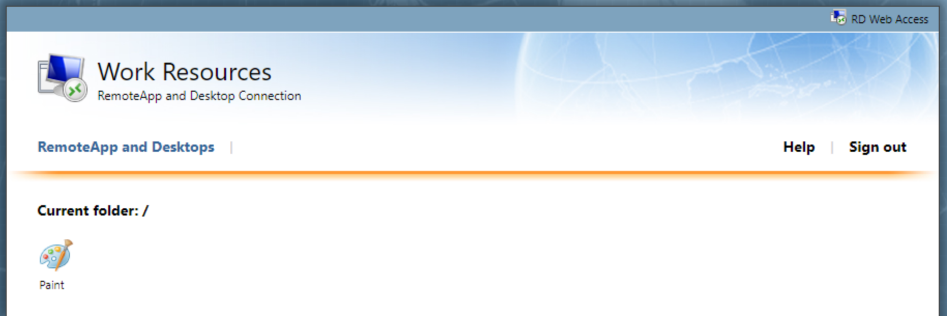 Open Paint application
Open Paint application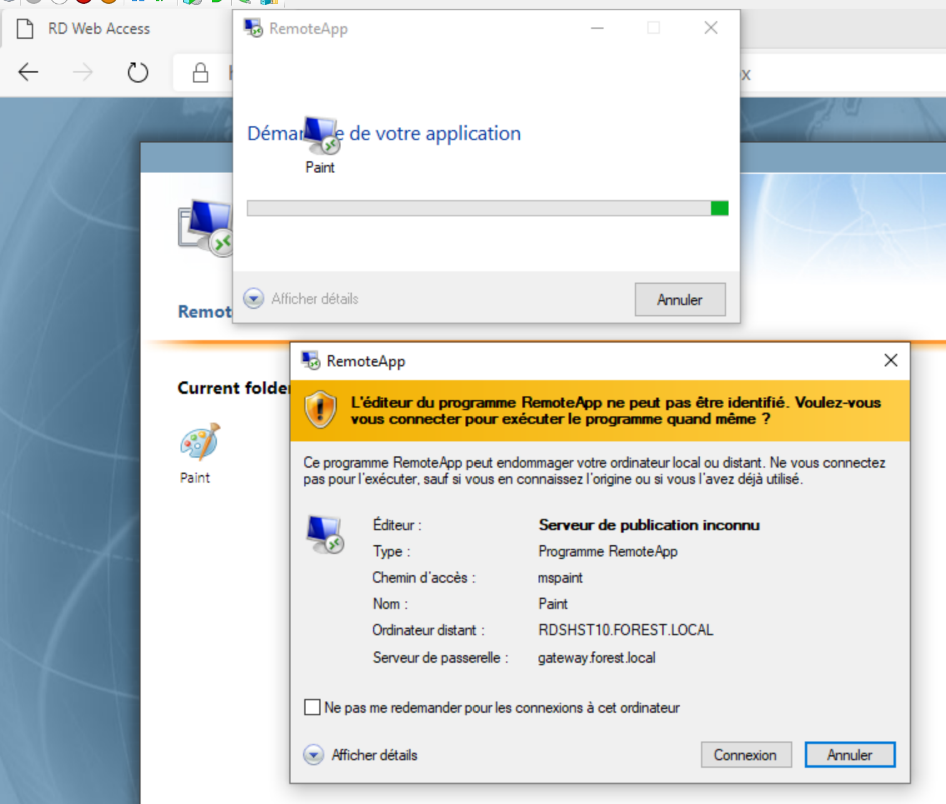 Click on « Connexion »
Click on « Connexion »
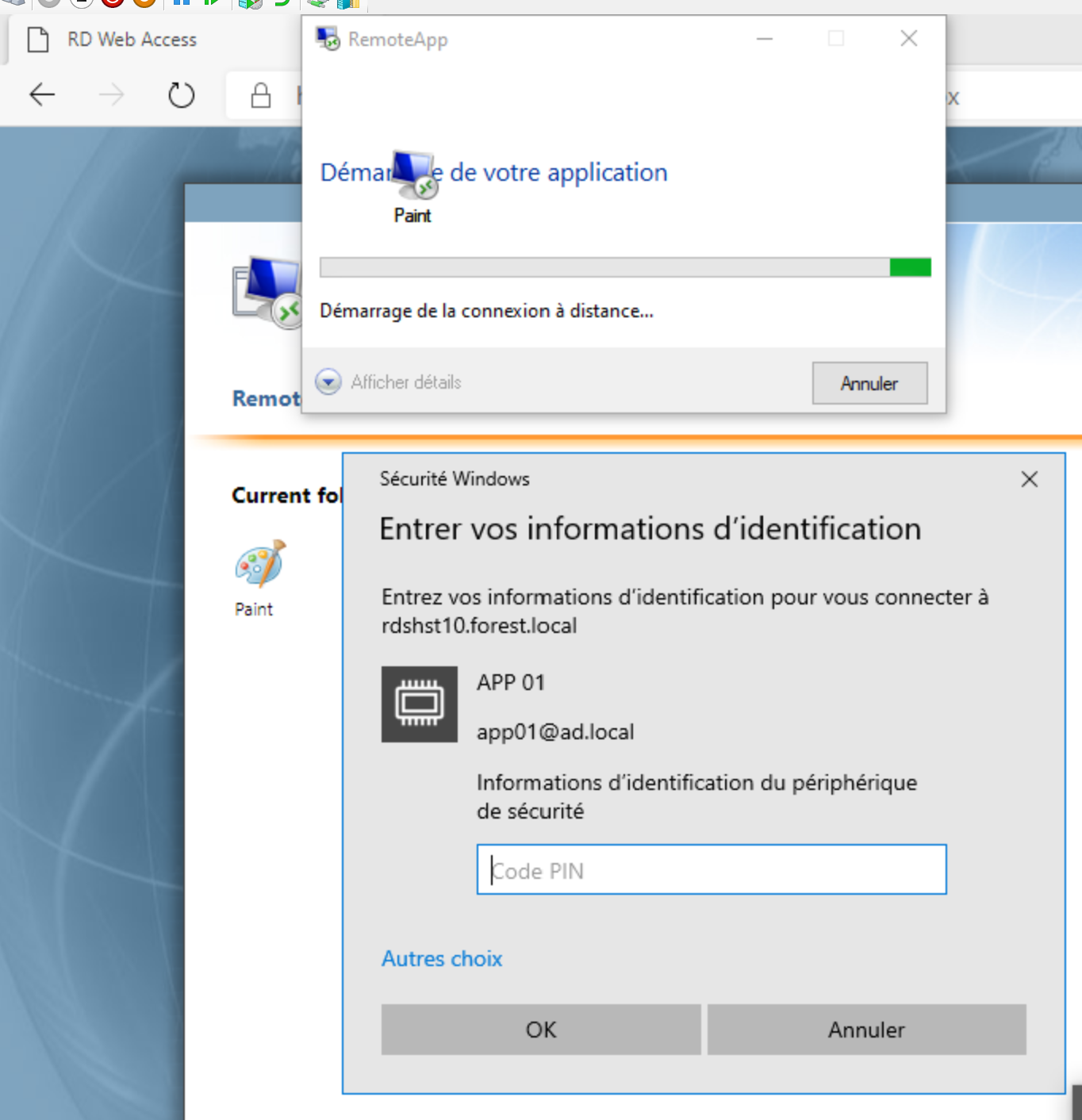 Enter smartcard code pin
Enter smartcard code pin
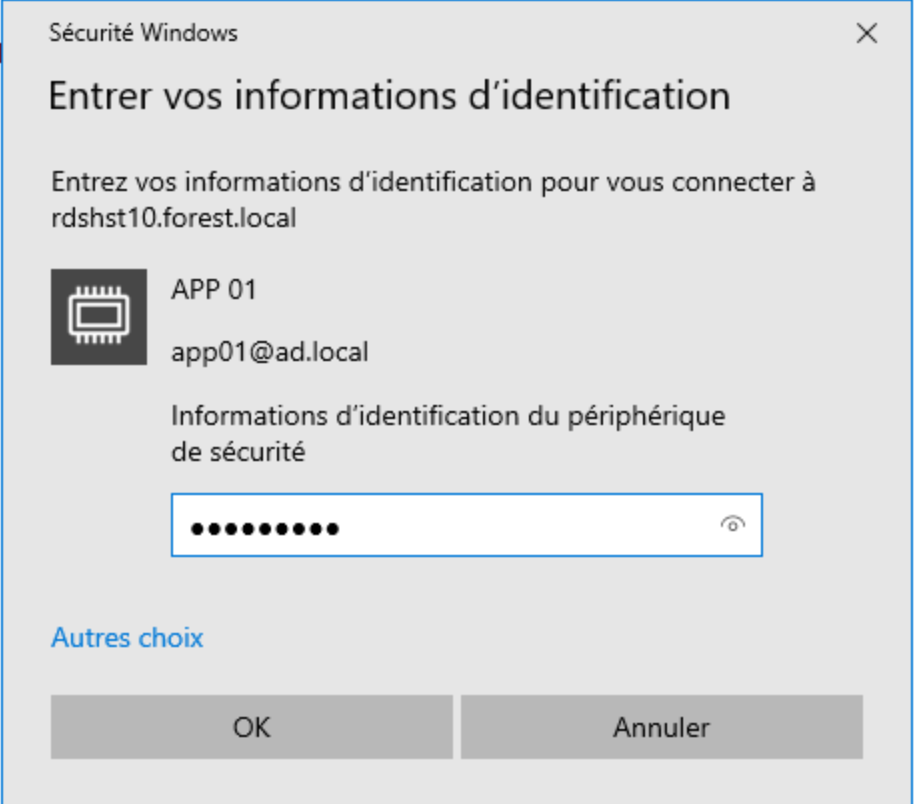 Click on OK
Click on OK
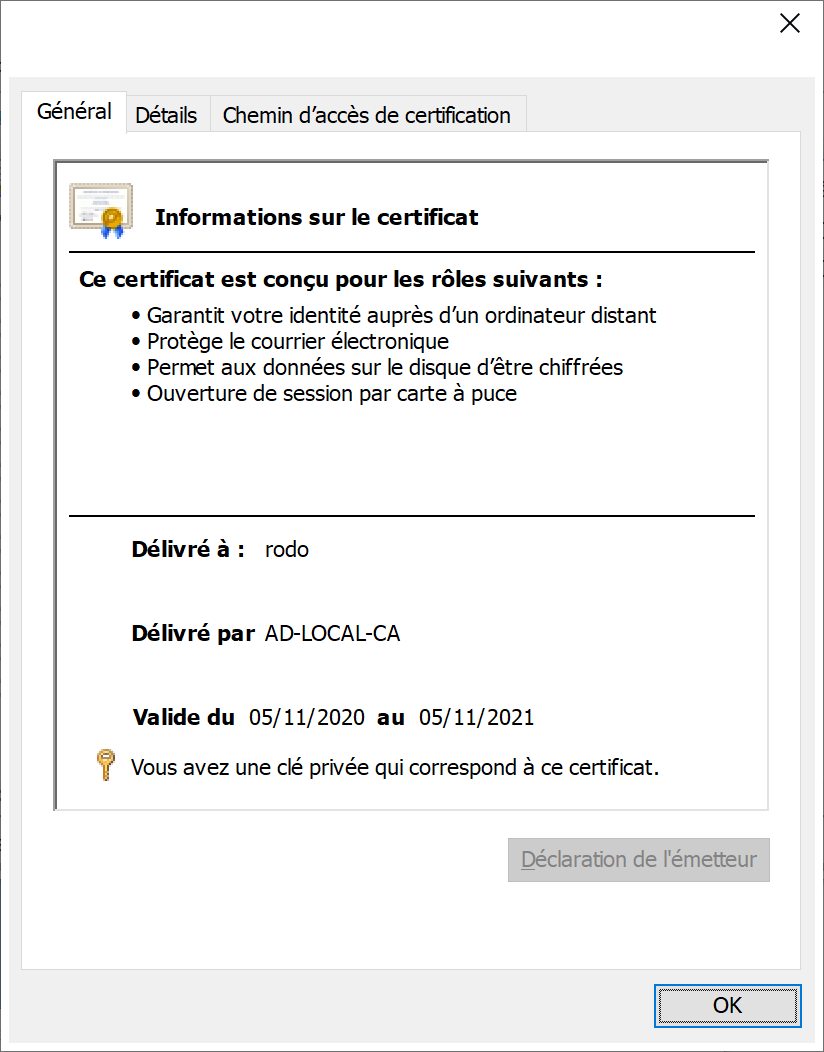
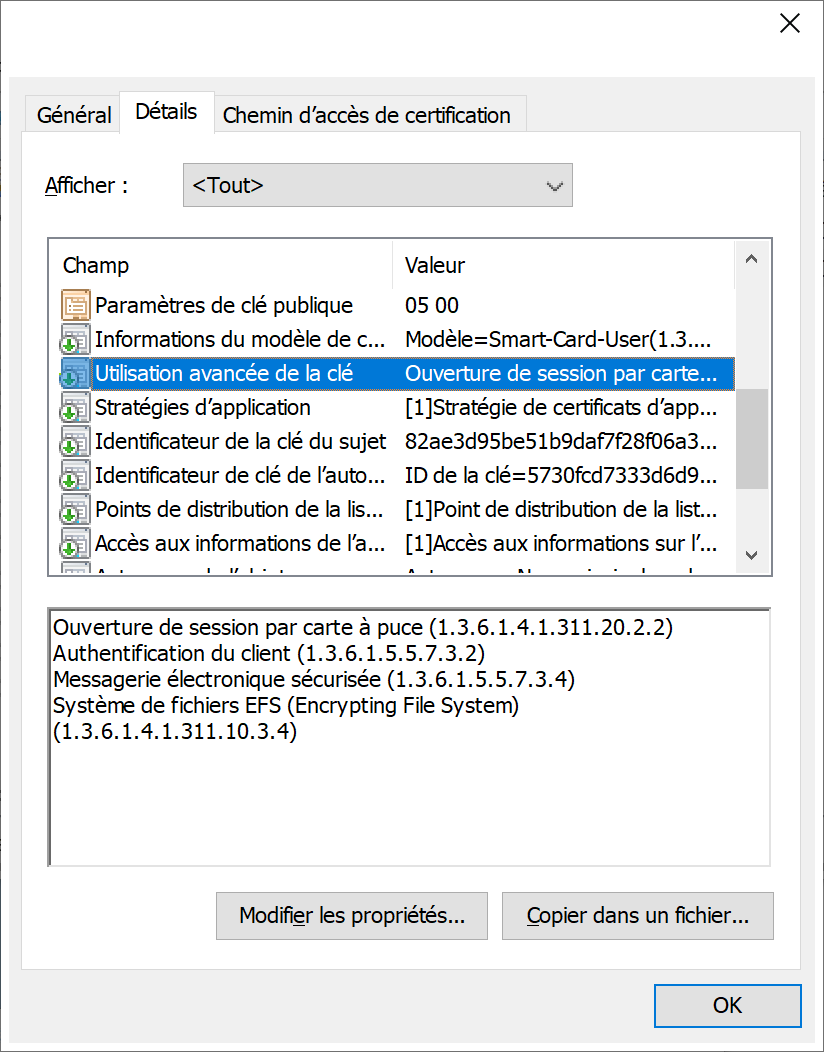
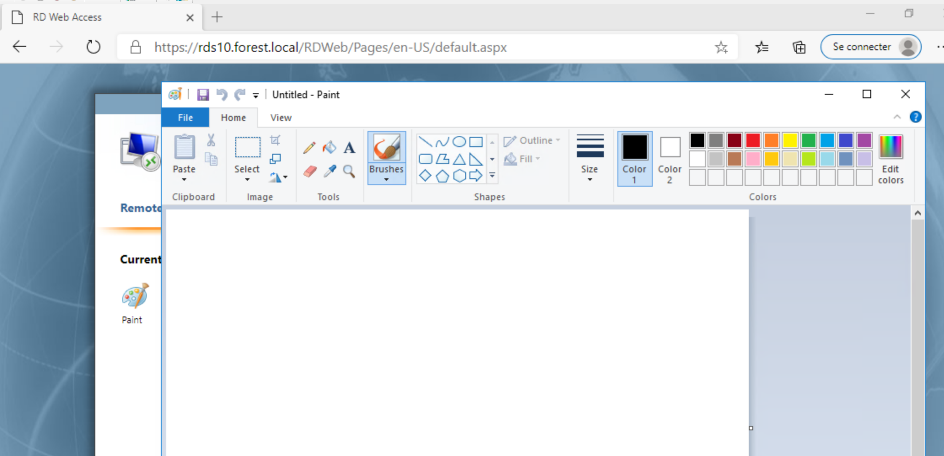 Application is open. Access is valid.
Application is open. Access is valid.
Test with Rodo Account for Calculator application
Open session on workstation Win10 with account user RODO
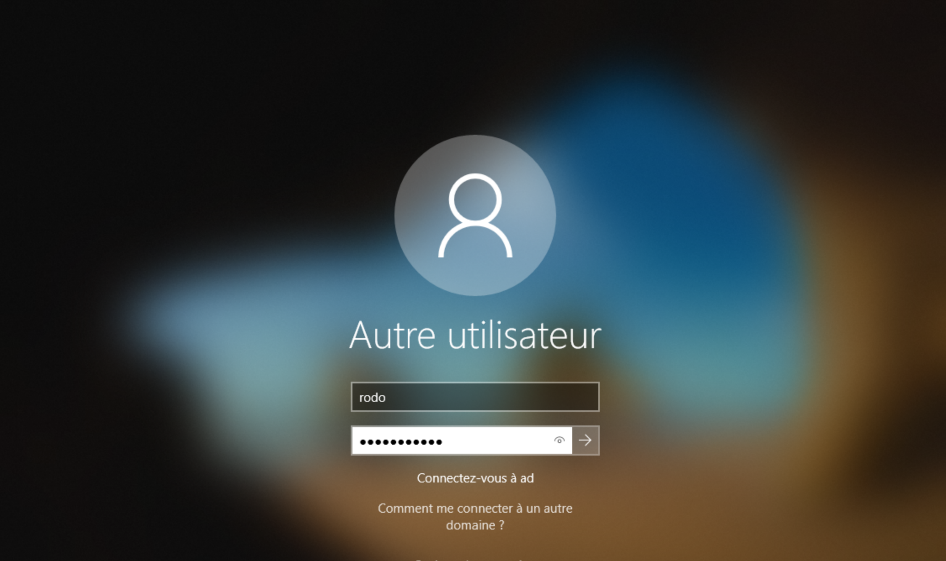 Open Edge browser and browse on url https://rds10.forest.local/rdweb portal
Open Edge browser and browse on url https://rds10.forest.local/rdweb portal
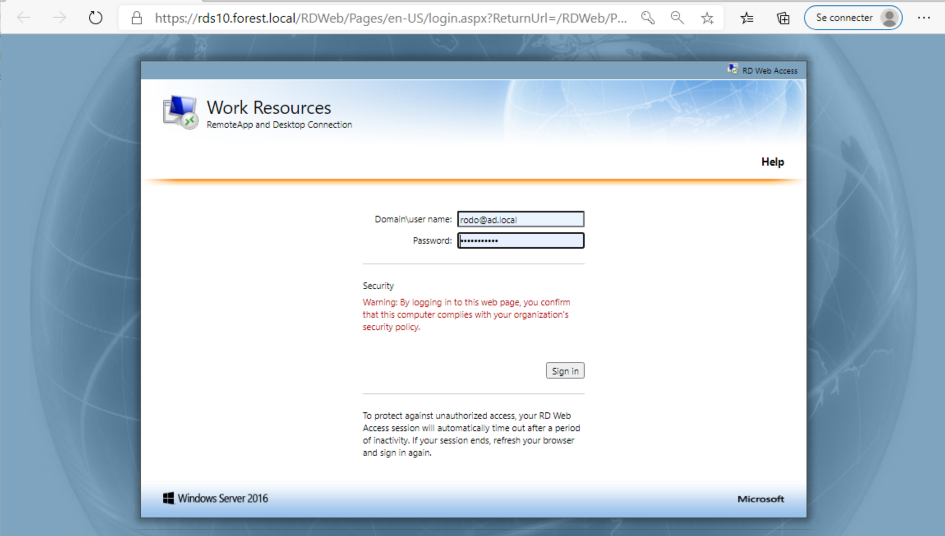 Open session with user account RODO
Open session with user account RODO
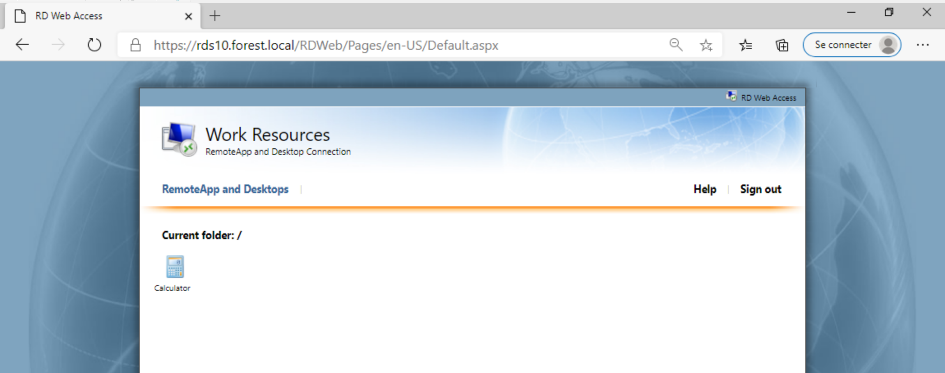 Open Paint application
Open Paint application
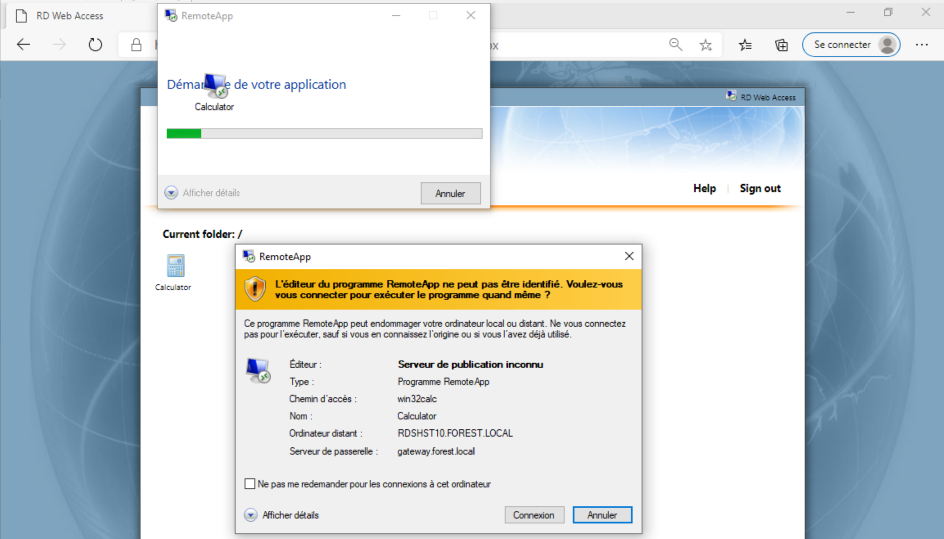 Click on « Connexion »
Click on « Connexion »
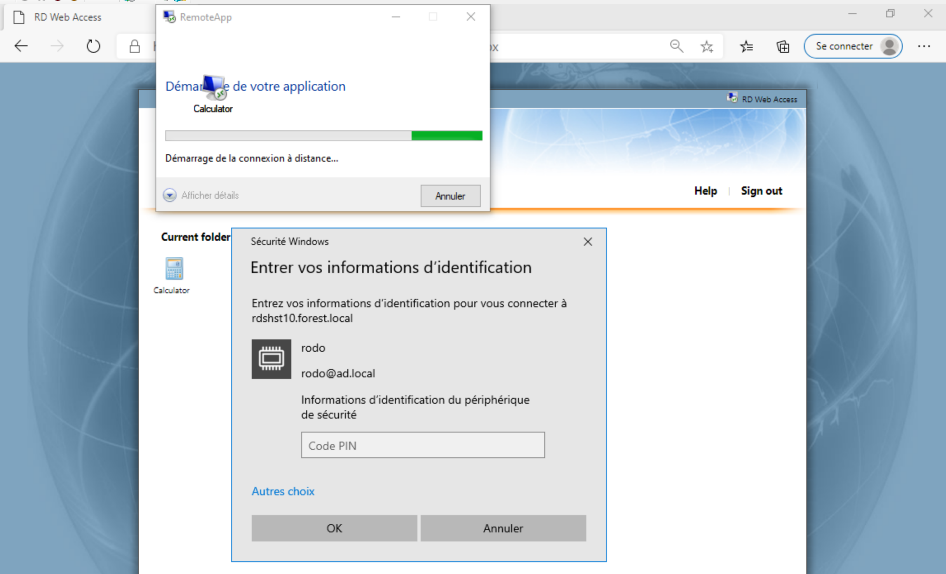 Enter smartcard code pin
Enter smartcard code pin
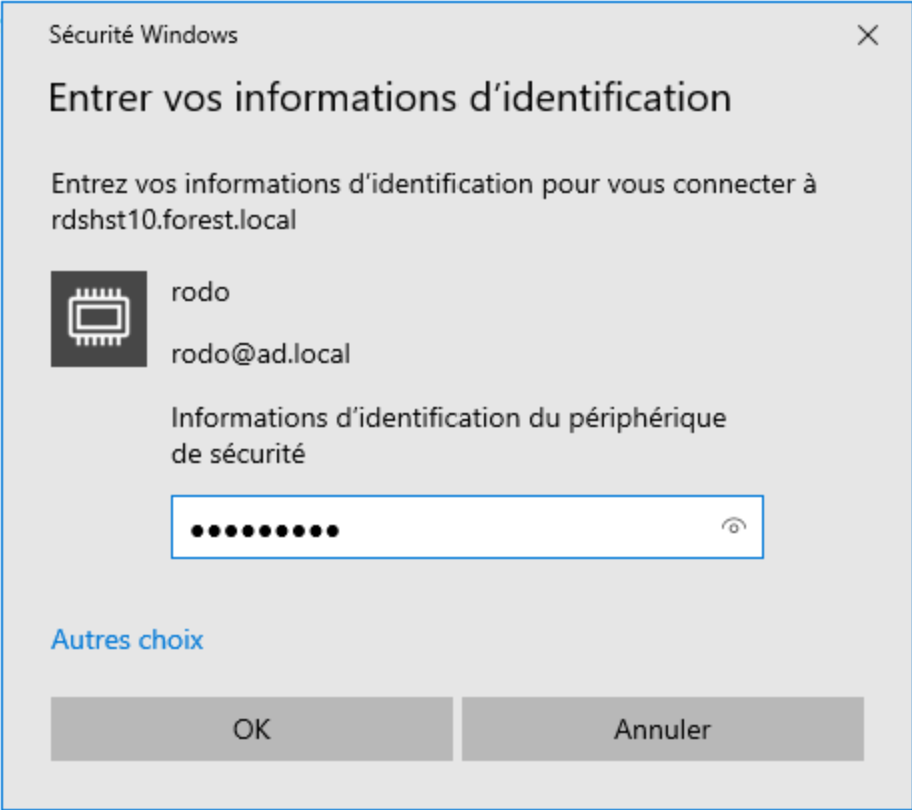 Click on OK
Click on OK
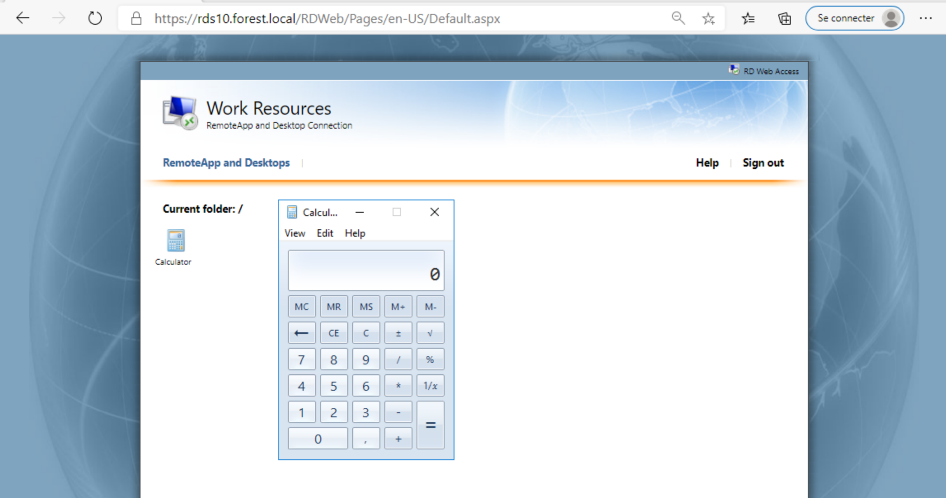 Application is open. Access is valid.
Application is open. Access is valid.